re | [羊城杯 2020]easyre
时间:2021-02-02 11:32:32
收藏:0
阅读:0
winx64的pe文件
估计是devc编译的,debugmode
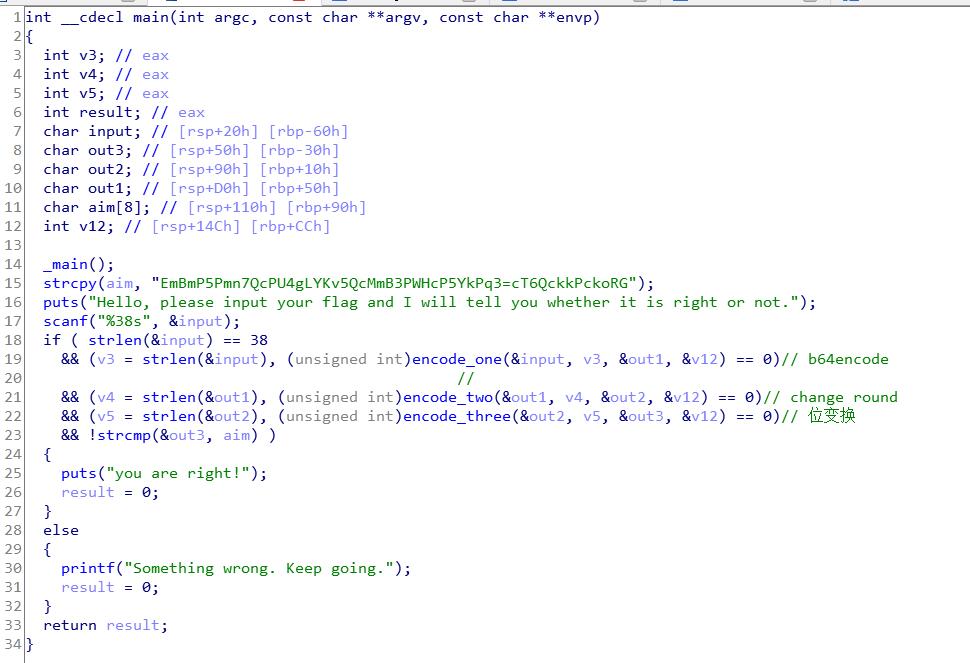
主要逻辑非常简单
base以后两个位变换
直接丢exp了:
from base64 import b64encode, b64decode
aim = "EmBmP5Pmn7QcPU4gLYKv5QcMmB3PWHcP5YkPq3=cT6QckkPckoRG"
p = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz01234567890+/="
count = len(aim)
print(count)
# 38位
flag = ""
# 从encode3开始爆破
tmp = ‘‘
for i in range(count):
print(i)
for j in p:
if ord(j) <= 0x40 or ord(j) > 0x5a:
if ord(j) <= 0x60 or ord(j) > 0x7a:
if ord(j) <= 0x2f or ord(j) > 0x39:
t = j
else:
t = chr((ord(j)-48+3)%10 + 48)
else:
t = chr((ord(j)-97+3)%26 + 97)
else:
t = chr((ord(j)-65+3)%26 + 65)
if t == aim[i]:
tmp += j
print(tmp)
break
print(tmp)
# BjYjM2Mjk4NzMR1dIVHs2NzJjY0MTEzM2VhMn0=zQ3NzhhMzhlOD
# encode2
_tmp = tmp[13:26] + tmp[39:] + tmp[:13] + tmp[26:39]
print(b64decode(_tmp))
overです。
评论(0)
